justpaint
gpt就是牛逼
先爆破五位数密码得到11452
然后让ai做ai
exp powered by chatgpt:
import torch
import torch.nn as nn
import numpy as np
import matplotlib.pyplot as plt
from PIL import Image
import cv2
class JBN(nn.Module):
def __init__(self):
super(JBN, self).__init__()
self.main = nn.Sequential(
nn.Linear(100, 256),
nn.ReLU(),
nn.Linear(256, 512),
nn.ReLU(),
nn.Linear(512, 452 * 280),
nn.Tanh()
)
def forward(self, x):
img = self.main(x)
img = img.view(-1, 452, 280)
return img
jbn = JBN()
jbn.load_state_dict(torch.load('jbn.pth'))
random_noise = torch.randn(1, 100)
jbn_img = jbn(random_noise)
jbn_img = jbn_img.squeeze().detach().numpy()
jbn_img = (jbn_img + 1) / 2 # 将图像像素值范围从[-1, 1]转换为[0, 1]
jbn_img = (jbn_img * 255).astype(np.uint8) # 将图像像素值转换为[0, 255]的整数
jbn_img = cv2.resize(jbn_img, (280, 452)) # 调整图像大小为452x280
flag_image = Image.fromarray(jbn_img)
flag_image.save('flag_restored.png')结果:
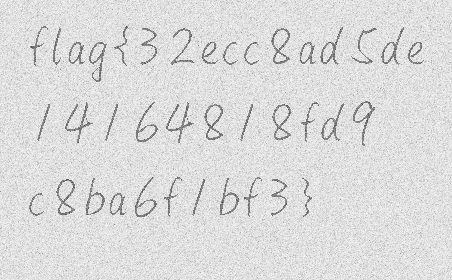
SecretZip
purezip.zip里面是ZipCrypto Deflate的算法,再加上题目描述,容易想到明文攻击,并且尝试后发现所给的key文件就是经过压缩的secret key.zip的前半段,于是直接拿来明文攻击
.\bkcrack -C purezip.zip -c "secret key.zip" -p key -o 0 >1.log由于给的够多所以跑的很快,密钥为e63af7cc 55ef839d dc10b922,直接解压
.\bkcrack -C purezip.zip -c "secret key.zip" -k e63af7cc 55ef839d dc10b922 -d 1.zip此时的zip是压缩之后的,得解压,直接cyberchef里面raw inflate
打开压缩包注释提示password is two bytes
直接zip2john接hashcat开爆,得到密码为$HEX[9c07]
随便写个脚本就给解压了,然后里面给了一串密钥,结合zpaq文件尾的提示,一眼丁真直接爆
bkcrack -k e48d3828 5b7223cc 71851fb0 -r 3 ?b得到密码

直接MD5再用bandizip解开zpaq压缩包就可以了
最套的一集
NoPasswd
拿到文档发现是加密的,并且office2john加hashcat加rockyou还爆不开
于是瞄一眼hex,发现了一些类似于宏的痕迹

直接就是一手oletools提取出vba脚本
olevba attachment.doc得到:
Sub XOREncryptFile()
Dim numbers(8) As Integer
numbers(0) = 19
numbers(1) = 71
numbers(2) = 122
numbers(3) = 99
numbers(4) = 65
numbers(5) = 111
numbers(6) = 43
numbers(7) = 67
Dim CurrentDirectory As String
CurrentDirectory = ".\"
If Dir(CurrentDirectory & "abc") = "" Then
Exit Sub
End If
Dim FileNumber As Integer
FileNumber = FreeFile
Open CurrentDirectory & "abc" For Binary Access Read Write As #FileNumber
Dim FileContent As String
FileContent = Input$(LOF(FileNumber), #FileNumber)
Close #FileNumber
Dim EncryptedContent As String
For i = 1 To Len(FileContent)
EncryptedContent = EncryptedContent & Chr(Asc(Mid(FileContent, i, 1)) Xor numbers((i - 1) Mod 8))
Next i
FileNumber = FreeFile
Open CurrentDirectory & "enc" For Binary Access Write As #FileNumber
Put #FileNumber, , EncryptedContent
Close #FileNumber
End Sub简单看看就知道是xor,被xor的字符串则猜测是文档最下面多出来的一串

于是直接拿到密码

打开文档除了一个zip的base64以外就没了
直接复制下来转成zip,但是怎么都解压不了
再仔细看看就知道开头文件名的长度有问题,改回08之后解伪加密即可

justlisten
hint.png汉信码扫出来得到oursecret的密码为0urS3cret
解开得到一串字符,猜测是某种表
abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890_}{-?!音频简单听一下后用Sonic Visualiser打开一眼就是十进制

懒得写音频相关的脚本了,直接左上角导出图片然后读像素
from PIL import Image
img = Image.open('1.png')
flag = []
for x in range(58,6561,17):
for y in range(868):
col = img.getpixel((x,y))[0]
if(col >= 210):
flag.append(y)
break
flgg = []
for i in flag:
if(i < 250):
print(0,end='')
elif(i < 280):
print(1,end='')
elif(i < 320):
print(2,end='')
elif(i < 350):
print(3,end='')
elif(i < 390):
print(4,end='')
elif(i < 430):
print(5,end='')
elif(i < 470):
print(6,end='')
elif(i < 520):
print(7,end='')
elif(i < 580):
print(8,end='')
else:
print(9,end='')得到了完整的十进制数据
0900030907000309100003100007100307100022277031005192203203432284426284735274836292742424842463147282734424837362942334460720080624061811100213180401000920140308111000181321001411220513021020010006211814083733362813100301092108201804080511070022131021010910032111041881000051310002215140514150005142926442845316448075218191108130662196162281413321042462081305141712001952141367676763然后脑洞一下,猜测是每两位int一下再去table里找相应的,超出范围的就舍去
table = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890_}{-?!"
a = "0900030907000309100003100007100307100022277031005192203203432284426284735274836292742424842463147282734424837362942334460720080624061811100213180401000920140308111000181321001411220513021020010006211814083733362813100301092108201804080511070022131021010910032111041881000051310002215140514150005142926442845316448075218191108130662196162281413321042462081305141712001952141367676763"
for i in range(len(a)//2):
try:
ii = a[2*i:2*i+2]
print(table[int(ii)],end='')
except:
continue于是得到了半边flag

再脑洞一下,删掉第一个字符再转一下,得到了另一半flag

最后根据语义拼接得到完整flag
DASCTF{Wh1stling_t0_Convey_informat1on!!!}(感觉像非预期?



